Introduction to “I2P”: Your own internet – secure, private and free
What should you do about misuse and exploitation of your personal data and values on the internet? A few years ago, even Sir Tim Berners-Lee turned away from his World Wide Web and is now on the road in the distributed new world with his “Solid” project. There is even more good news: it is quite easy to turn to the modern, distributed world and use the free internet, for example via “I2P”. We show you how.
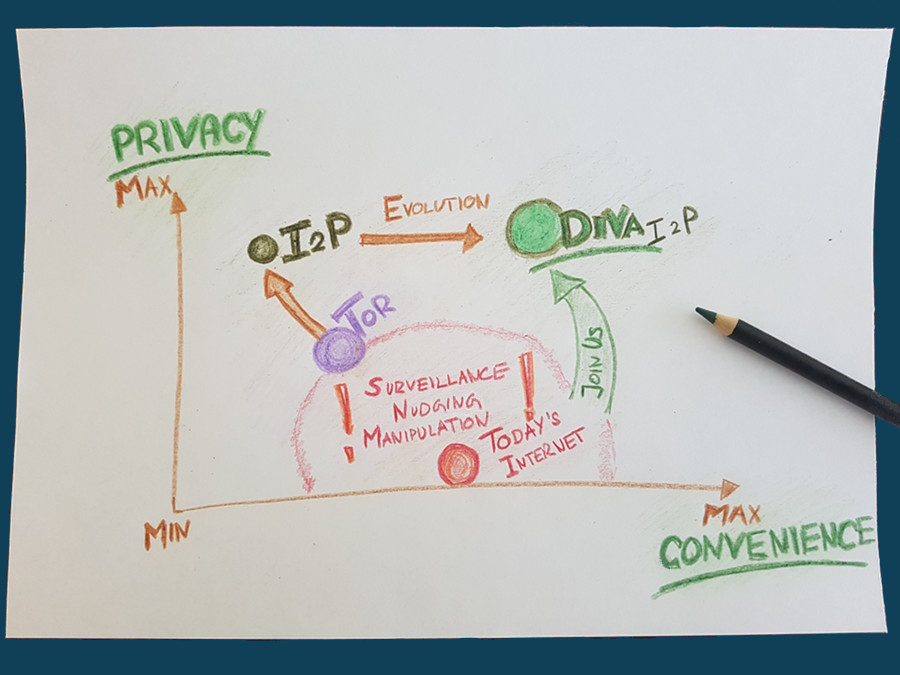
The path: Tor and I2P
From the point of view of technology nerds, the path to their own, secure and private internet has been difficult: in the past 15 years, many wrong turns have been taken and many painful lessons had to be learned. For example, a considerable number of regular users currently see the “Tor browser” as an way to use the internet in a private manner. But the “Tor network” is rather centralized and has some weak points. Today, many Tor users are actively discriminated against and are barred from using services. The reason: Infrastructure and service providers can easily identify gate traffic and block, harass or censor users. “I2P”, a distributed and censorship-resistant network, is only known to few. Manipulators or regulators often refer to it in a pejorative manner as the “darknet”. I2P is simply the free internet from people for people. Of course, the entire I2P development is unconditionally open source.
As soon as a user accesses I2P, the user automatically becomes an I2P node – and part of a modern “grassroots movement”. That is the beauty of this free network: it is a give-and-take. Many of these users participate privately, for example on their own laptop or mobile phone. Incidentally, the developers of I2P work continuously protective measures against node discrimination. In other words, other network participants (for example a telecommunications company or a monitoring system) should not be able to see whether and where an I2P node is being operated. All these efforts, which have lasted more than a decade, are now beginning to bear fruit.
Further development
This grassroot movement is gaining momentum. The obvious misuse of networks, devices and software by authorities and companies concerns many people. The intangible or material expropriation and paternalism in combination with abuse of power is no longer acceptable to many citizens. For these reasons, users become part of a grassroots movement – simply by using the free internet. Fortunately, technology expertise has grown steadily over the past 30 years. Nowadays, it is possible for most users to use “I2P” or “Tor” and thus make smarter technology decisions.
DIVA.EXCHANGE, for example, has drawn up, instructions for interested beginners how they can operate an I2P node or gate access on any computer. These instructions can be found below.
Outlook
The free internet is growing, and thus I2P with all its serious and honest possibilities for application. More and more users are making a small part of their computing capacity and bandwidth available. That is the grassroot movement. But there is also a need for better and simpler applications on the free internet. DIVA.EXCHANGE, for example, takes care of free banking technology. Easy-to-use social networks – such as Mastodon – or means of communication such as chat should be available on the free internet. This is the mission today: basic technologies are ready – next the needs of users in terms of “convenience and simplicity” have to be met! We at DIVA.EXCHANGE are happy about anyone who wants to join in and helps to advance on these goals.
Related Links
Instructions for beginners in I2P, English: https://github.com/diva-exchange/i2p
Public chat of the DIVA.EXCHANGE community, German and English: https://t.me/diva_exchange_chat_de
Privacy, simply explained: https://www.diva.exchange/en/privacy/privacy-simply-explained/
Give your feedback : https://social.diva.exchange/@social
Solid (Social Linked Data), https://en.wikipedia.org/wiki/Solid_(web_decentralization_project)
Tor Browser, https://en.wikipedia.org/wiki/Tor_(anonymity_network)#Tor_Browser
I2P, https://en.wikipedia.org/wiki/I2P
Instructions – How to use I2P and Tor
These instructions show how to set up a “container” on your own computer, which grants access to both the free and the known internet. A container is a neutral, isolated environment on your own computer. A container is fundamentally secure – at best as secure as the underlying operating system, of course. In any case, it is preferable to install new software that you want to test or use in a container than to install it directly.
The technology for containers is called “Docker”. For Mac, Windows or Linux you can get Docker here: https://docs.docker.com/get-docker/. A worthwhile introduction for those interested in technology can be found here (approx. 10 minutes to read): https://docs.docker.com/get-started/overview/.
Set up a Docker container
For those users on Windows or Mac who have never used “Docker”, “Powershell” or “Shell”: the 10-minute entry-level video for Docker on Windows or Mac is worth watching.
After installing Docker, you fetch the DIVA.EXCHANGE container. This fetching process is called “pull”. The following commands are executed in the Powershell (Windows) or in the Shell (Linux or Mac). Thus, the first step is to fetch the container with:
docker pull divax/i2p:current-i2p-torThen initiate the container with the following command:
docker run --env PORT_TOR=9950 --env PORT_HTTP_PROXY=4544 --env ENABLE_HTTPPROXY=1 -p 7170:7070 -p 4544:4444 -p 9950:9050 -p 8080:8080 -d --name i2p-tor divax/i2p:current-i2p-torAfter a few seconds, the container and thus the free internet will be available. For the very first initiation, “I2P” takes about three minutes to fully integrate into the network. You can use this time right away to set up your own favorite browser (see below).
You can stop the container at any time with:
docker stop i2p-torYou delete the container completely with:
docker rm i2p-torA deleted container is re-initiated with the “docker run” command above.
You start a stopped container with:
docker start i2p-torIf you switch off the computer, you have to restart the container after rebooting the computer.
Set up a browser
To set up your own favorite browser (Firefox, Chrome, Safari etc.), open it and then select “settings”. In the “settings” you look for “proxy”.
There you set the “Automatic proxy configuration via URL” and set the value to:
http://localhost:8080/proxy.pacFinished! Close settings and start surfing. The settings in the browser look something like this:
A “proxy” is nothing more than a “place in between”. We want to use the container set up above as a “place between browser and Internet”. Our new container redirects our traffic either via I2P to the free internet or via Tor to the known internet. And exactly this redirection point is “localhost: 8080”. In other words: our own computer, door number 8080 – and this door leads to our own container.
If you now surf the well-known internet, such as https://diva.exchange or https://www.ft.com/, Tor is automatically used and privacy is much better protected. The free internet, for example http://diva.i2p, is then also available as usually in the browser. By the way, in the free internet you don’t need “https” for – i.e. .i2p addresses, such as diva.i2p. All traffic is encrypted locally in the container with your own, self-created key. This is at least as secure as “https”.
Final comments
This simple guide is a first step into the free internet for interested beginners. However, to protect your privacy in the digital space, you need a lot more and extensive reading. Basic add-ons such as “Adblock Plus”, “uBlock” or “NoScript” should be installed and activated in any case.
As always and everywhere, you need to take note: swindlers and chatterboxes in all shapes and colors are present and active – often very well masked. It is therefore essential to check any information several times and independently.
